Table of Content
- 1. Why This Domain Triggers Search Interest
- What usually leads users to search internetchicks.com-
- Common assumptions vs reality-
- Search trends and curiosity patterns-
- 2. First-Impression Signals That Matter
- Domain behavior and loading patterns-
- Redirects, ad density, and browser warnings-
- Trust indicators that are present vs missing-
- 3. Content Classification Without Exposure
- High-level categorization of content style-
- What the site avoids disclosing upfront-
- Boundary clarity and moderation signals-
- 4. Reviews Showing a Risk Lens
- 1. Malwarebytes / ThreatDown-
- 2. Scam Detector-
- 3. ScamAdviser-
- 4. Gridinsoft-
- 5. What Real Users Complain About Repeatedly
- Aggregated issues discussed by users-
- Repeated red flags-
- Gaps between expectation and delivery-
- 6. Privacy, Data & Device Safety Assessment
- Tracking behavior indicators-
- Risk of unwanted downloads or scripts-
- Impact on device security and personal data-
- 7. Who Should Avoid internetchicks.com Completely
- Specific user groups at higher risk-
- Situations where visiting is strongly discouraged-
- Bottom-Line Reality Check
- Clear safety conclusion-
- Risk vs reward summary-
- Final cautionary guidance-
1. Why This Domain Triggers Search Interest
Search interest around internetchicks.com does not behave like interest around mainstream platforms, brands, or services. Users rarely search this domain out of curiosity about features, pricing, or community. Instead, search behavior overwhelmingly points to post-exposure verification.
What usually leads users to search internetchicks.com-
In most cases, users encounter the domain indirectly, not intentionally. Common entry points include:
● Clicking a link embedded in unrelated websites
● Being redirected after interacting with ads or pop-ups
● Seeing the domain blocked or flagged by a browser, DNS filter, or security extension
● Finding it listed in a security alert, firewall log, or antivirus warning
Only after this encounter do users search the domain name to understand:
● What the site is
● Whether it is safe
● Why it appeared without deliberate intent
This “after-the-fact” behavior is a strong indicator of risk-oriented curiosity, not genuine interest.
Common assumptions vs reality-
A frequent assumption is that if a site:
● loads successfully,
● uses HTTPS,
● and looks visually functional,
then it must be reasonably safe.
In reality, technical accessibility does not equal trustworthiness. HTTPS merely encrypts data in transit; it does not verify business legitimacy, ethical sourcing, or safe advertising practices. Many high-risk domains function perfectly at a surface level while still exposing users to:
● aggressive tracking
● misleading ad funnels
● harmful redirect ecosystems
This gap between appearance and actual risk is a key reason users seek clarification after exposure.
Search trends and curiosity patterns-
Traffic analysis platforms show that internetchicks.com receives substantial direct traffic volumes rather than brand-led or informational keyword traffic. This pattern is consistent with:
● redirected users
● repeated short visits
● low intentional discovery
In other words, people are not “choosing” the site — they are landing on it and then verifying whether they should have.
This is a classic behavioral signature of domains that exist within monetized traffic loops, not trust-driven ecosystems.
2. First-Impression Signals That Matter
When assessing a domain from a risk standpoint, first impressions are not aesthetic — they are behavioral and infrastructural.
Domain behavior and loading patterns-
Security vendors such as Malwarebytes have documented internetchicks.com as being associated with riskware-style behavior. This classification typically applies when a domain is observed to:
● act as an intermediary in redirect chains
● funnel users toward potentially unwanted programs (PUPs)
● participate in deceptive ad delivery mechanisms
Importantly, this does not require the site itself to host malware. Participation in the delivery pipeline is sufficient to raise concern.
Redirects, ad density, and browser warnings-
Users commonly report:
● unexpected redirects
● pop-unders
● security warnings before or after page load
Such warnings are not arbitrary. Modern browsers and security tools rely on reputation scoring, historical abuse patterns, and community reporting. A warning usually indicates repeatable risk, not a one-off incident.
Domains that consistently trigger alerts across different tools have crossed a threshold of collective risk recognition.
Trust indicators that are present vs missing-
Present (limited value):
● HTTPS encryption
● Functional loading behavior
Missing (high-impact gaps):
● Clear ownership attribution
● Transparent operating entity
● Easily accessible legal and safety documentation
● Visible moderation or compliance standards
Reputation platforms like ScamAdviser often show mixed scores for such domains — technically functional but flagged for caution due to missing accountability signals.
In a risk audit, what is missing matters more than what is present.
3. Content Classification Without Exposure
This assessment avoids describing or reproducing content. The goal is classification, not exposure.
High-level categorization of content style-
Multiple third-party reviews and safety analyses place internetchicks.com within a high-risk adult aggregation category. This classification is important not because of content type, but because of structural risk factors commonly associated with such ecosystems:
● content aggregation rather than original creation
● unclear sourcing and consent validation
● monetization-first architecture
Sites operating in this category often prioritize traffic flow and ad yield over transparency or user protection.
What the site avoids disclosing upfront-
Risk-focused analysis consistently notes the absence of:
● clear explanations of content sourcing
● statements on consent verification
● moderation or takedown mechanisms
● accountability or dispute resolution paths
This lack of disclosure does not prove wrongdoing, but it prevents users from making informed decisions before exposure.
Boundary clarity and moderation signals-
High-trust platforms clearly communicate:
● who content is for
● what is allowed
● how issues are handled
Low-trust platforms often defer or obscure these boundaries, relying instead on generic disclaimers. The absence of strong boundary signaling is itself a risk amplifier, especially in regulated or ethically sensitive categories.
4. Reviews Showing a Risk Lens
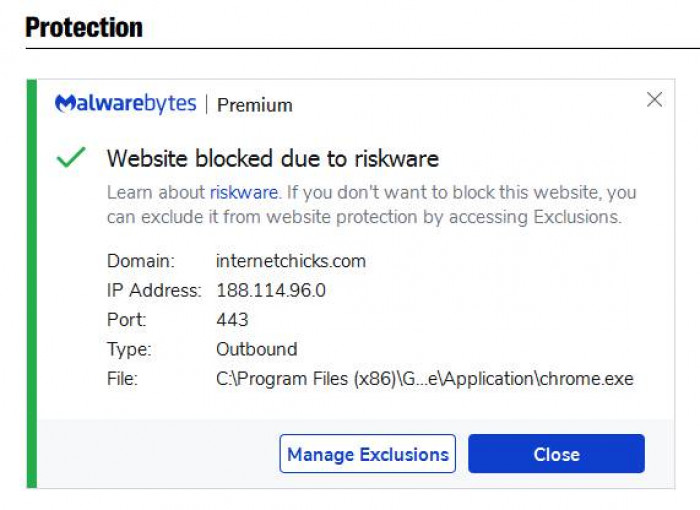
1. Malwarebytes / ThreatDown-
1. Status: Blocked
2. Classification: Riskware-associated domain
3. Reason: Linked to adware / PUP / redirect-based risk behavior
4. Impact: Users may be redirected to unwanted or deceptive destinations
5. Type of signal: Hard security block (strong negative)
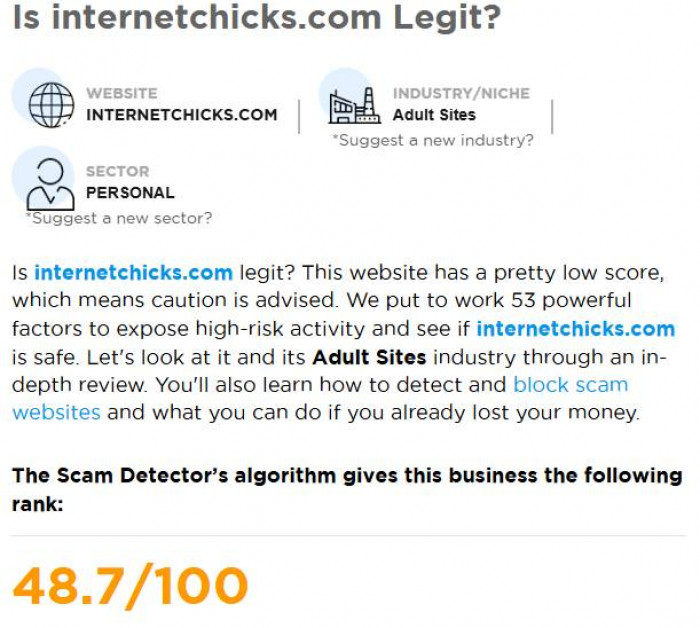
2. Scam Detector-
1. Trust score: 48.7 / 100
2. Label: Doubtful – Medium Risk – Alert
3. Methodology: Score based on 53 risk indicators
4. Type of signal: Algorithmic risk rating (negative)
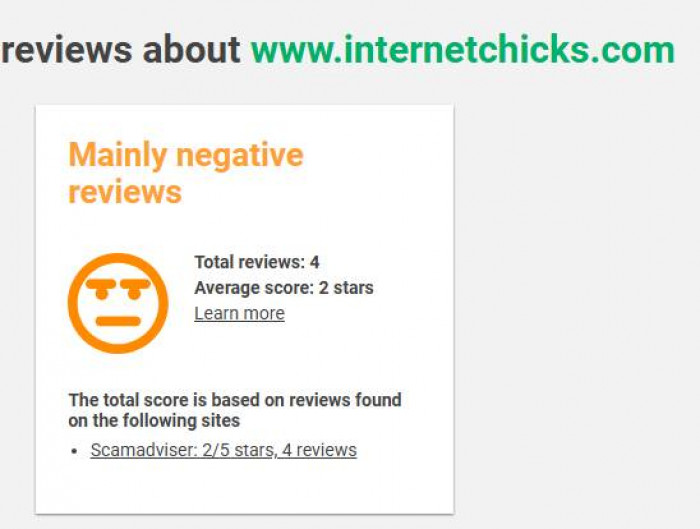
3. ScamAdviser-
1. User reviews: 4 total
2. Average rating: 2 / 5 stars
3. Key note: Automated system flags “looks safe,” but user feedback is mainly negative
4. Type of signal: Low-volume but negative user sentiment
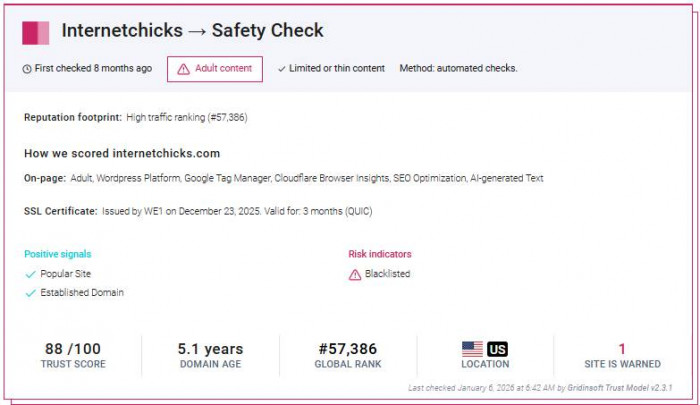
4. Gridinsoft-
1. Trust score: 88 / 100
2. Risk note: Domain listed as blacklisted within Gridinsoft’s system
3. Cross-engine scan:
a. Many antivirus engines → Clean
b. Gridinsoft → Warned
4. Type of signal: Mixed (clean malware scan, but reputational concern)
5. What Real Users Complain About Repeatedly
Direct user testimonials are fragmented, but patterned complaints emerge across forums, comments, and reputation platforms.
Aggregated issues discussed by users-
Common themes include:
● landing on the site unintentionally
● difficulty exiting without redirects
● warnings from security software
● discomfort with unclear site intent
These complaints are less about content and more about loss of control.
Repeated red flags-
The repetition of:
● security warnings
● redirect reports
● ad-related frustration
across unrelated users and platforms suggests systemic issues rather than individual misconfigurations.
Gaps between expectation and delivery-
Users expect:
● a normal web experience
● predictable navigation
● transparency
What they encounter instead:
● forced pathways
● unclear purpose
● elevated security concern
This expectation gap is one of the strongest indicators of low trustworthiness.
6. Privacy, Data & Device Safety Assessment
Privacy risk does not require explicit data theft to be meaningful.
Tracking behavior indicators-
Domains embedded in aggressive ad ecosystems often rely on:
● third-party tracking scripts
● cross-site identifiers
● behavioral profiling
While specific trackers may vary, the environment itself elevates privacy exposure.
Risk of unwanted downloads or scripts-
Security write-ups emphasize that the risk is not always a visible download. It can include:
● notification permission abuse
● background scripts
● deceptive prompts
These can lead to persistent device-level annoyance or vulnerability.
Impact on device security and personal data-
Even without malware, exposure can result in:
● browser hijacking symptoms
● notification spam
● increased phishing exposure
Once permission is granted accidentally, reversal can be difficult for non-technical users.
7. Who Should Avoid internetchicks.com Completely
Specific user groups at higher risk-
● Minors
● Users on work, school, or shared devices
● Individuals without strong security tools
● Users previously affected by adware or notification spam
Situations where visiting is strongly discouraged-
● After an unsolicited redirect
● When a browser or antivirus blocks the site
● On mobile or in-app browsers
● On networks with compliance requirements
Bottom-Line Reality Check
Clear safety conclusion-
From a risk-audit perspective, internetchicks.com safety is questionable. Multiple independent signals indicate elevated exposure risk.
Risk vs reward summary-
● Reward: minimal informational value
● Risk: redirects, privacy exposure, device-level nuisance, ethical uncertainty
Final cautionary guidance-
If you did not deliberately seek this domain, do not interact further. If research is required, rely on indirect analysis tools rather than live browsing.
Avoidance is the rational choice.


